SOC 2 Compliance Implementation Support
Scale and build trust with your customers by being SOC 2 compliant
Supporting New Zealand and Australian businesses get through their first-ever SOC 2 Compliance audits with 100% confidence.
Getting started is challenging, hence why our dedicated cybersecurity specialists will guide you through the process and provide pre-audit assessments to make sure you are on the right path to achieving your SOC 2 attestation report.
Our dedicated consultant will be with you through all the stages, right from conducting gap assessments, implementation, audits and maintaining your security and compliance posture.
We work with amazing customers




Unlock better revenue opportunities with a SOC 2 Type 1 or Type 2 Reports.
At AMARU, our specialists will assist you through your SOC 2 compliance journey making sure you get your SOC 2 report at a much faster rate than if you were to do it in-house. We work with a range of external accreditation auditors making your selection process easier, faster and cost effective. Our comprehensive end-to-end managed security services are designed to ensure cyber risk management and a successful outcome for your business so you can build and run secure products and services.
TIMELINE TO ACHIEVE YOUR SOC 2 ATTESTATION REPORT
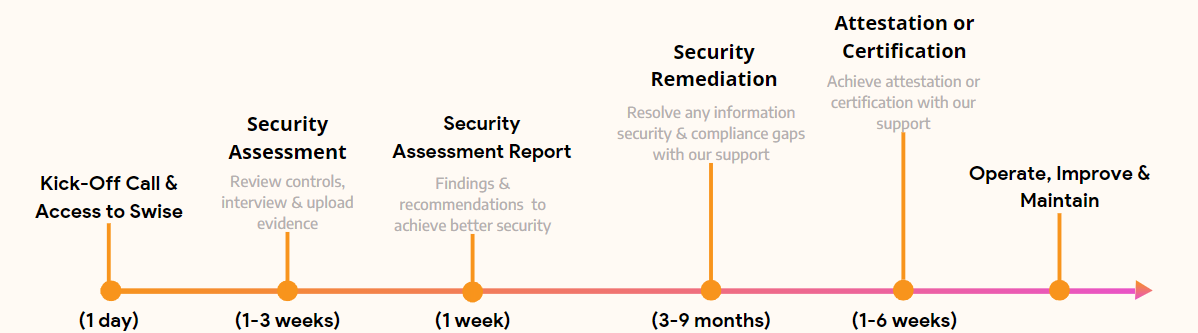

Here’s how AMARU fits into your SOC 2 compliance journey
Not all businesses have the time and resources to have an in-house compliance officer or CISO. This is where AMARU’s expertise comes in. We work as your security and compliance team, making sure you get the support you need and work with the auditors from an accredited American Institute of Certified Public Accountants (AICPA) firm to accelerate your compliance.
As you grow your business, systems become more complex and it is painful for you to manually track and manage cybersecurity and compliance across people, technology and processes. Our services are technology-enabled to help you plan, achieve and manage security and compliance at a much faster rate. Our services are enabled by our cyber security and compliance platform Swise.ai.
As part of our end-to-end services, we make sure you get a clean SOC 2 report and ensure you have the right controls post the audit.
How does SOC 2 Compliance Benefit Organisations?
Businesses in fast-moving and modern environment can enhance cyber resilience proactively, minimising organisational risk exposure, and align with top-tier cyber security standards with a SOC 2 Report.

Enhanced Data Security
SOC 2 compliance provides a robust framework for enhancing data security, safeguarding your business and customer information, ultimately reducing the risk of significant cybersecurity gaps.
Competitive Advantage
Achieving SOC 2 compliance sets your business apart, keeping you ahead of your competition in terms of demonstrating a commitment to industry-recognised security standards and best practices.

Increased Trust
Having a SOC 2 report is becoming an expectation among customers. You can build trust and credibility with customers, partners, and stakeholders by showcasing your dedication to data security and compliance.
Case Study

Figured were facing high demand with third party due diligence and security expectations from partners. Working with financial institutions they needed a security accreditation to give their partners and customers confidence in their security. They knew that they needed SOC 2 attestation but didn’t know if they had the expertise to achieve it. They are a young, dynamic company and needed a partner that could understand their needs and fit into their company culture.

Frequently Asked Questions
See our frequently asked cyber security questions below for help and advice.
What is a SOC 2 report?
SOC 2 is a compliance framework that validates your organisation’s information security practices. It is most commonly used in North America and particularly obtained by SaaS companies. A SOC 2 report is a document that will verify your SOC 2 compliance. An AICPA-accredited auditor provides the SOC 2 report to evaluate your data security and document the SOC 2 controls you’ve implemented. A report will then be created which will consist of the findings and attestation as to whether your organisation meets SOC 2 criteria or not.
What is the difference between SOC 2 Type 1 and SOC 2 Type 2 report?
The main differences between a SOC 2 Type 1 and Type report lies in:
Audit Scope:
A SOC 2 Type 1 only needs to cover the design of your controls, whereas a SOC 2 Type 2 must cover the design and operating effectiveness of your controls.
Audit Speed:
A Type 1 report takes place a lot faster than a Type 2. Once you have the SOC 2 controls implemented, you can immediately have an auditor start the SOC 2 Type 1 audit. However, SOC 2 Type 2 requires an audit period and organisations need to wait until the audit period has passed to start the audit. This means that it will take a while until your customers or prospects can gain access to the report.
Audit Cost:
SOC 2 Type 1 report requires lower time and effort, therefore the cost is also less. Mid-sized companies can expect to pay starting from $7K for a Type 1 audit report. The cost of a Type 2 report is significantly higher as more time and effort goes into it.
Reporting Cadence:
SOC 2 reports need to be renewed on an annual basis as a standard practice. These reports do not expire, however, the information may be less relevant over time. A SOC 2 Type 2 report from three years ago may no longer contain the most relevant information on your company, and specifically the security at your company.
What are the benefits of obtaining SOC 2 Compliance report?
Becoming SOC 2 compliant can have multiple benefits on your business. Benefits include increased trust and confidence from clients, better risk management, a competitive edge in the marketplace, and assurance of data security and privacy practices. With cyber risk insurance becoming more and more expensive, showcasing a SOC 2 report can help with lowering of long-term costs and expensive fines, if a potential data breach were to occur.
How long does implementing SOC 2 take?
The timeline for achieving SOC 2 compliance can vary, but generally for SOC 2 Type 1 Audit it evaluates the design of an organisation’s security controls at a specific point in time and this typically can take upto 2-4 months to complete, including preparation, audit fieldwork, and report generation.
As for SOC 2 Type 2 Audit, it evaluates the operating effectiveness of an organisation’s security controls over a period of time, therefore, it can take up to 3-9 months including the audit period, preparation and audit fieldwork to generate a SOC 2 Type 2 report.
The key factors that influence the timeline are:
- The complexity of the organisation’s systems and controls
- The availability and responsiveness of the organisation’s staff during the audit process
- The auditor’s workload and availability
- Budget allocated to the project
What industries and entities need to be SOC 2 compliant?
SOC 2 compliance can be relevant to all organisations, but it’s particularly useful for “service organisations.” Service organisations that store customer data in the cloud, manage sensitive information, or provide services related to financial transactions, healthcare, or technology often need to be SOC 2 compliant.
As most New Zealand and Australian businesses are small-to-medium sized enterprises, jumping on this journey to get compliant can be difficult and overwhelming. Which is why, we offer a highly effective service where we’d take care of all your security and compliance requirements as part of your team.
How does AMARU support organisations in obtaining SOC 2 compliance?
AMARU provides Australian and New Zealand businesses a comprehensive support in the compliance process, including readiness risk assessments, policy and procedure development, implementation of security controls, and preparation for SOC 2 audits. We also work with together with the auditors, to answer all the questions and get you SOC 2 compliant in no time.
We started our SOC 2 journey internally but are struggling at the moment. Can you help?
Yes, we specialise in helping businesses achieve security compliance standards no matter where on the implementation journey they are. We also understand the struggle, which is why we’d be happy to work with you on making sure you get the process right at the first time.
Apart from that, maintaining all the information, and keeping track of documentation manually can be highly time consuming. With our service you also get access to our in-house AI-powered platform Swise.ai which can help you manage the compliance process with automated integrations to lessen your workload and keep your documentation up to date.







