Automatic Security Operations & SIEM
Intelligence-driven and AI-powered SecOps platform.
Monitoring, logging and managed services for Australia and New Zealand businesses with applications and systems running on Google Cloud and beyond.
Apply Google’s threat intelligence to uncover and defend against the latest threats
Elevate your team’s talent and productivity with generative AI

We work with amazing customers





Detection

Investigation

Hunting

Threat Intelligence
Automation & AI
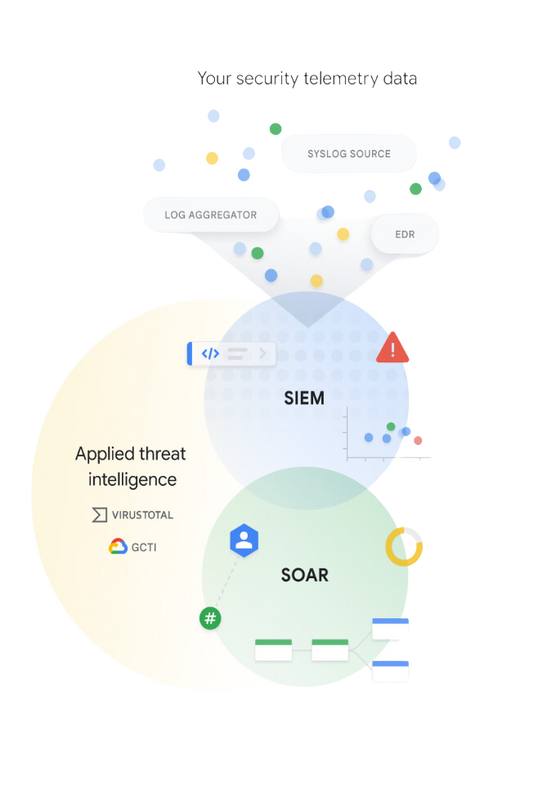
AMARU’s Security Operations is built on Google infrastructure to provide reliable performant and secure cloud-computing services to businesses across A/NZ region. We help businesses utilise our Security Operations for a unified experience across SIEM, SOAR, and utilise the threat intelligence to drive better detection, investigation, and response.
Collect security telemetry data
Apply threat intel to identify high priority threats
Drive response with playbook automation, case management, and collaboration.
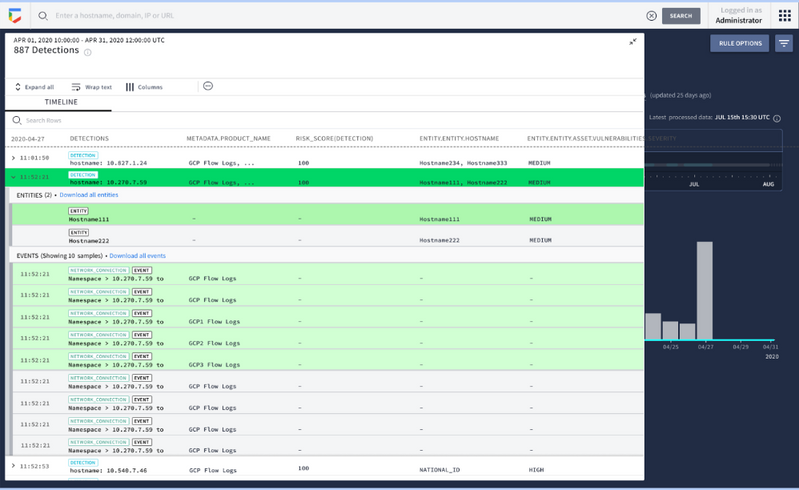
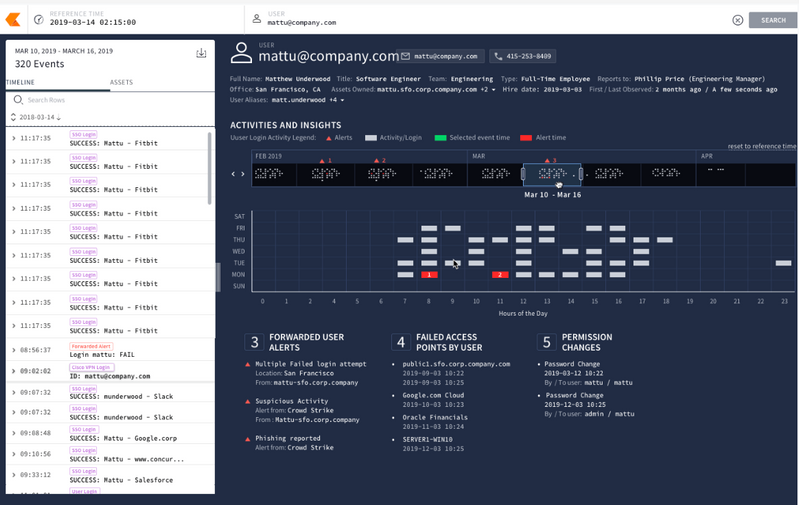
Detect threats with confidence
This service will help you simplify detection creation with YARA-L for custom content. Businesses can harness intelligence from Google, Mandiant, and VirusTotal to automatically reveal potential threats and you’ll be able to receive early warnings of active breaches using Mandiant’s frontline intelligence.
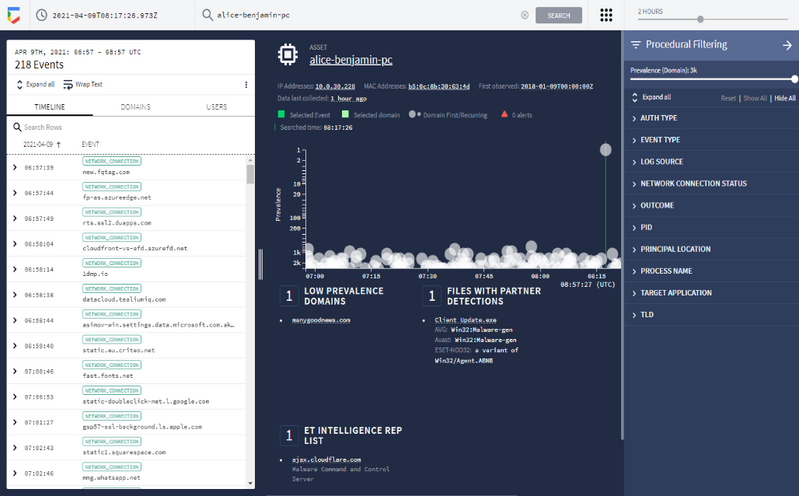
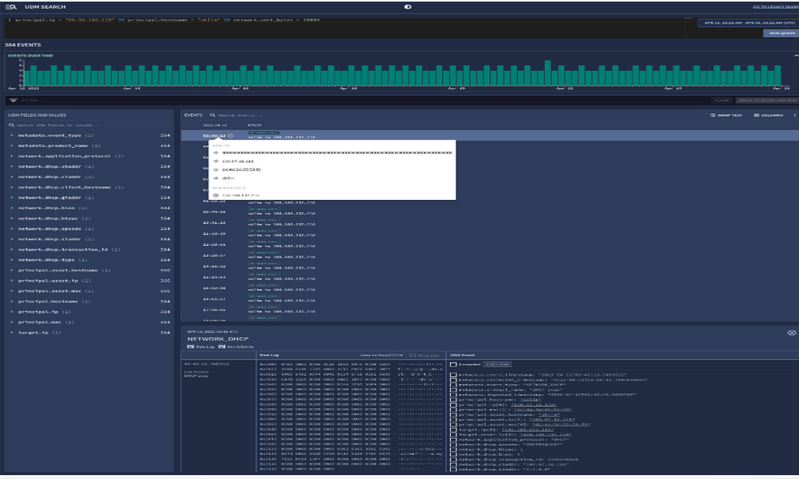
Investigate with easy access to insights
With the SecOps platform, businesses can analyse real-time activity with investigation views, threat intel insights and user aliasing.
We help manage, priortise, and assign work with unique threat-centric case management.
Respond in no-time with precision
Through this platform, we’ll be able to drive consistency and automate repetitive tasks with a full-featured intuitive playbook builder and 300+ integrations.
We can also easily collaborate on every case with your business analysts, service providers, and other stakeholders.
Enhance productivity with generative AI
This enables natural language search, iteration, and drill-down of data using Gemini, which generates underlying queries and provides full mapped syntax.
Users can interact with AMARU SecOps through a context-aware AI-powered chat, which includes the ability to create detections and playbooks.
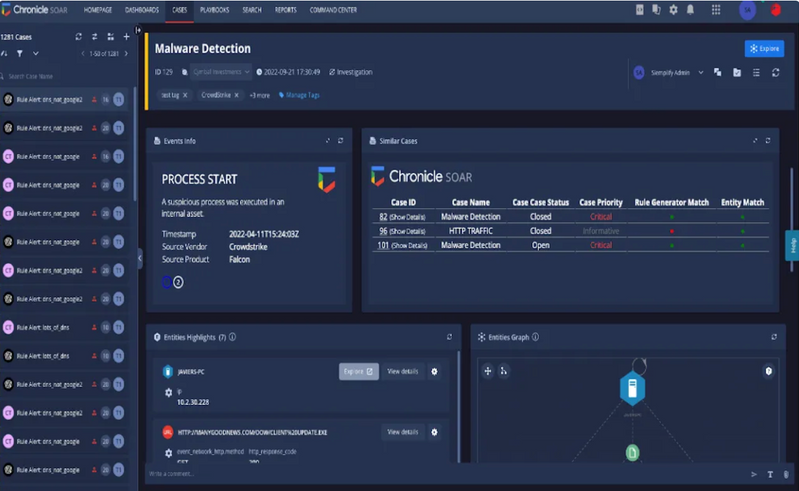
Augment your team with expert help
We partner with Mandiant elite threat hunters to seamlessly hunt for hidden attackers using your data. Gain complete visibility and actionable insights into their search techniques, findings, and mapping to the MITRE ATT&CK® framework.
Kick start with modern SecOps today
Bringing to all New Zealand and Australian businesses, a modern approach to threat detection, investigation, and response
Hyperscale cloud infrastructure
This allows us the ability to analyse any volume of telemetry, lightning fast search option across large data and 12 months of hot retention.
Applied threat intelligence
Ability to use threat intelligence sources like Mandiant and VirusTotal to get high-quality insights about threats that unlock deeper threat hunting and investigation workflows
AI-powered innovation
Infuse Gemini into your security operations to better understand threats, reduce toil, and uplevel talent and use natural language to generate search queries.







