With large-scale breaches exposed in Q1 and Q2 of 2024 and there will be inevitably more to come, the global landscape is primed for more stricter regulations around cyber security governance and compliance.
Australia passed the privacy legislation amendment act to introduce large fines for privacy breaches. New Zealand made changes to its privacy laws, increasing penalties for businesses who are non-compliant from $2000 to $10,000. This would help organisations to build better resilience, businesses will need to align to global standards.
There are a number of different cyber security frameworks available that can provide your business with a structured, measurable and proactive approach to mature your cyber security, protect your assets and minimise the impact of cyber threats.
Benefits of aligning to a cyber security framework

Source: Pexels
1. Improving security posture
Aligning to a cybersecurity framework will help you to systematically identify and mitigate vulnerabilities, thereby enhancing your overall security posture. By implementing established guidelines and best practices, you can proactively address potential threats, reduce the likelihood of breaches, and improve your incident response capabilities.
2. Trust
Adopting a recognised cybersecurity framework builds trust among stakeholders, including customers, partners, and regulatory bodies. When you demonstrate your commitment to adhering to industry standards, it signals to stakeholders that you prioritise security and data protection. This trust leads to stronger business relationships, customer loyalty, and a positive reputation in the marketplace, ultimately contributing to competitive advantage.
3. A standardised approach
A cybersecurity framework provides a standardised approach to managing security risks. This consistency ensures that all team members understand their roles and responsibilities in maintaining security, reducing the chances of oversight or miscommunication. A standardised framework also facilitates benchmarking against industry best practices, enabling organisations to measure their security maturity and identify areas for improvement.
4. Risk management
Cybersecurity frameworks offer comprehensive risk management strategies that help you assess, prioritise, and address risks effectively. By following a structured approach, you can identify potential threats, evaluate their impact, and implement appropriate controls to mitigate those risks. This proactive stance can enable you to make informed decisions about resource allocation and security investments, ultimately leading to better risk management outcomes.
5. Meeting compliance requirements
Aligning to a cybersecurity framework can aid you in meeting various compliance requirements, such as ISO 27001, HIPAA, PCI-DSS, and others. Many regulatory bodies recognise established frameworks as benchmarks for compliance, simplifying the process of adhering to legal and regulatory obligations. By integrating these frameworks into your operations, your business can ensure they are not only compliant but also prepared for audits and assessments, reducing the risk of penalties and reputational damage.
Types of frameworks:
New Zealand and Australian government frameworks

CERTNZ’s Critical Controls
CERT NZ’s critical controls are designed to help you decide where to spend your time and money based on the data and insights they receive from reports and international threat feeds.
Many of their controls start by encouraging you to identify your assets. This identification is fundamental in any security operation because it’s difficult to protect systems and infrastructure if you don’t know they exist.
The controls include patching software and systems, using multi-factor authentication, building security awareness with your employees, and offering a practical list of controls to focus on.
Reference: CERT NZ’s Critical Controls
Australian Cyber Security Centre’s ‘Essential Eight’
The Essential Eight is a series of mitigation strategies, developed by the Australian Cyber Security Centre (ACSC) to help protect Australian businesses from cyber threats.
The Essential Eight framework, defines four maturity levels from maturity level zero through to maturity level three based on an increased ability for you to mitigate more complex tactics and techniques used by malicious actors and provide a great roadmap for maturing your security posture over time.
Reference: Essential Eight Framework
NZISM – New Zealand Information Security Manual
The New Zealand Information Security Manual was specifically written by the New Zealand Government to provide guidance on how government agencies should manage personnel, information, and physical security. Baseline controls detailed in the document are the minimum acceptable level of controls that should be applied to all government systems.
The manual defines explicitly what policies and configurations should be set and gives guidance on whether the controls are optional (should) or mandatory (must).
This manual has tended to lack the perspective of real world application and often fails to take into account user experience, but can be a great guideline of what to strive for.
You can reference the NZISM here ISM Document | New Zealand Information Security Manual (gcsb.govt.nz)
Global Frameworks
NIST Cybersecurity Frameworks
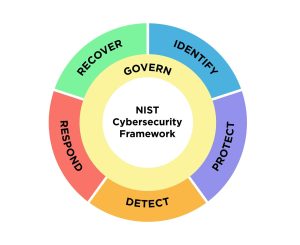
The NIST Cyber Security Framework is a flexible and voluntary framework developed in the US that you can adopt to manage and reduce cyber security risk. It consists of five core functions: Identify, Protect, Detect, Respond, and Recover. This highly popular framework also involves implementation tiers to help you assess and track your maturity level over time and works towards aligning the core functions with specific business requirements.
Reference: NIST CSF
ISO 27001 Standard
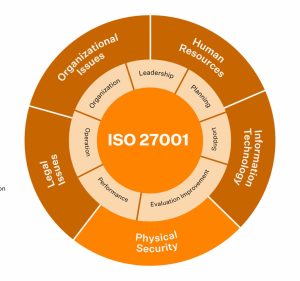
The ISO 27001 is a standard for Information Security Management Systems (ISMS). An ISMS is a framework of policies, processes, procedures and controls used to manage and protect an organisation’s information assets.
The ISO 27001 standard provides guidance for establishing, implementing, maintaining and continually improving an organisation’s ISMS and proactively identifying and addressing weaknesses. It’s an internationally recognised standard, making it the choice for organisations that want to have a globally recognised, comprehensive security certification.
Reference: Information security, cybersecurity and privacy protection.
Strategic/Business approach Framework
NCSC Cyber Security Framework
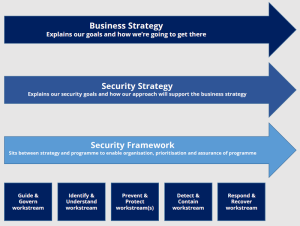
The National Cyber Security Centre has released a beta version of their Cyber Security Framework. The framework sets out how we think, talk about, and organise cyber security efforts. Its five functions represent the breadth of work needed to secure an organisation.
The framework is founded on the NIST framework but adds a local New Zealand perspective to address our diversity needs around securing Māori data and meeting Treaty partner’s security expectations.
The framework’s five functions are Guide & Govern, Identify & Understand, Prevent & Protect, Detect & Contain and Respond & Recover.
Reference: NCSC’s Cyber Security Framework
How can we help?
AMARU’s team specialises in helping businesses plan, implement and manage security and compliance. If your team is unsure on what frameworks would suit best for your business requirements or you’ve decided on the framework and are looking for a compliance partner to guide you on the implementation process, reach out to our specialists and we’d be happy to help!


