CrowdStrike’s new 2024 Global Threat Report has been creating some buzz around the latest trends in the cyberattacks, and we are here to make the key takeaways from the main topics that were talked about in the report more accessible to you.
To summarise, the cyberattacks ecosystem have been increasing and here are certain figures to keep in mind-
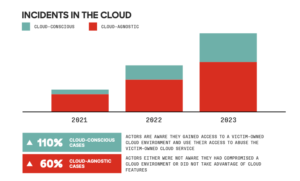
CrowdStrike recorded 34 new adversaries in 2023 with an increase of 75% in the Cloud environment intrusions and 110% cloud-conscious cases year over year mostly with financial motives. According to the data, the technology industry was most frequently targeted followed by telecommunication and financial with highest interactive intrusion of 61% in North America and 4% in the Oceania region.
Uncovering the Stealthy Adversaries
Tracking over 230 adversaries, the CrowdStrike 2024 Global Threats Report reveals an alarming increase in the speed and stealth of cyber attacks. Adversaries are adapting and operating with unprecedented stealth, making it harder for defenders to detect security breaches. the report showcases the rising threat of identity-based attacks, the dominance of adversaries in the cloud, and the exploitation of vendor-client relationships to access multiple victims. Additionally, the use of generative AI by adversaries raises concerns on the sophistication of future cyberattacks.
Highlights from the CrowdStrike’s 2024 Report
Let’s delve into the 2024 Global Threat Report by CrowdStrike offers several key takeaways that businesses need to be aware of:
1. Identity-based and social engineering attacks on the rise.
Despite advancements in cybersecurity landscape, identity-based and social engineering attacks remain prevalent. Threat actors continue to exploit human vulnerabilities to gain unauthorised access to sensitive information. Phishing campaigns, credential theft, and social engineering techniques are commonly used by attackers. For instance, the FANCY BEAR threat actor targeted Yahoo! Mail and ukr.net webmail users by using a custom toolkit that intercepted multifactor authentication credentials.
2. Cloud-environment intrusions increased by 75% from 2022 to 2023.
Cloud computing has become an integral part of modern business operations, but it has also attracted the attention of threat actors. In 2023, cloud-environment intrusions saw a significant increase of 75% compared to the previous year. Cybercriminals are targeting cloud environments to gain access to corporate networks. CrowdStrike’s analysis reveals that financial motives drive 84% of these intrusions, while targeted attacks account for the remaining 16%. It is now evident that adversaries’ preference for identity-based techniques is on cloud-focused attacks.
Source: CrowdStrike Global Threats Report 2024
3. Exploit trusted third-party relationships to gain initial access into the organisation
Exploiting trusted relationships with third-party service providers or software vendors has become a popular strategy among threat actors.CrowdStrike highlights two key techniques- 1st being comprising the software supply chain using trusted software to spread malicious tooling and 2nd being leveraging access to vendors supplying IT services.
This approach offers a high ROI for attackers and poses a greater risk to organisations, especially those operating in the technology sector. For example, the JACKPOT PANDA threat actor used a trojanized installer for a popular chat application to infect users with malware or North Korea’s Supply Chain Compromises. This will likely motivate attackers to continue throughout 2024 as well.
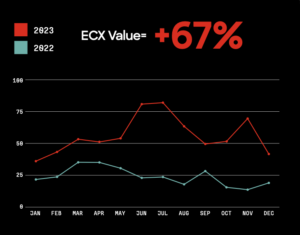
4. Attackers are compromising networks at a faster rate.
Once threat actors gain an initial foothold in a targeted network, they aim to move laterally and expand their access within the network. CrowdStrike’s report highlights that the breakout time for interactive eCrime intrusion activity has decreased from 84 minutes to 62 minutes between 2022 and 2023. Attackers are becoming more efficient in their operations, utilising stolen credentials, exploiting trusted relationships, and relying on malware-free activities to bypass detection.
Source: CrowdStrike Global Threats Report 2024
5. Attackers are targeting periphery networks.
With the increasing use of endpoint detection and response sensors, threat actors have adjusted their tactics to target the network periphery. Edge gateway devices and other devices that are not closely monitored or updated pose vulnerabilities that attackers exploit. Vulnerabilities in firewalls, VPN platforms, and outdated devices are common targets for attackers. It is crucial for organisations to prioritise patching and updating these exposed products and eliminate End of Life (EOL) products from their networks.
2024 Threats on the Horizon
As we prepare for the potential threats that might emerge in 2024, two key areas highlighted in the report, that come to forefront is 1. Generative AI and 2. 2024 global government elections.
With Generative AI opportunities would arise on developing and execution of malicious computer network operations (CNO) and supporting the efficiency and effectiveness of social engineering campaigns. As Generative AI speedily gains popularity, the cyber activities are likely to increase as well this year.
2024 is also the year of more 42% of the world population participating in the general elections that will take place in 55 countries. This also makes it the year where adversaries will gain numerous opportunities to target entities that are involved in the process throughout the year.
Recommendations for mitigating these cybersecurity risks
In light of these key takeaways, CrowdStrike provides several recommendations to help organisations mitigate cybersecurity risks:
- Implement phishing-resistant multifactor authentication (MFA) and extend it to legacy protocols.
- Educate employees about social engineering techniques and conduct regular awareness programs.
- Deploy technology that can detect and correlate threats across identity, endpoint, and cloud environments.
- Prioritise the use of Cloud Native Application Protection Platforms that provide comprehensive monitoring and threat detection capabilities.
- Adopt a consolidated security platform that offers complete visibility across all security domains.
- Patch exposed products promptly and eliminate EOL products from the network.
By following these recommendations, organisations can enhance their cybersecurity posture and better protect their critical assets from evolving threats.
Disclaimer: AMARU is an official partner of CrowdStrike.


