We work with amazing customers




What is Essential Eight?
The Essential Eight is a series of mitigation strategies, developed by the Australian Cyber Security Centre (ACSC) to help protect Australian businesses from cyber threats.
This is a great guide for implementing security best practices, and can be used to establish a security baseline and plan for improvement. This gives you assurance that you have in place the most important features and controls to help better protect your systems, data and people.

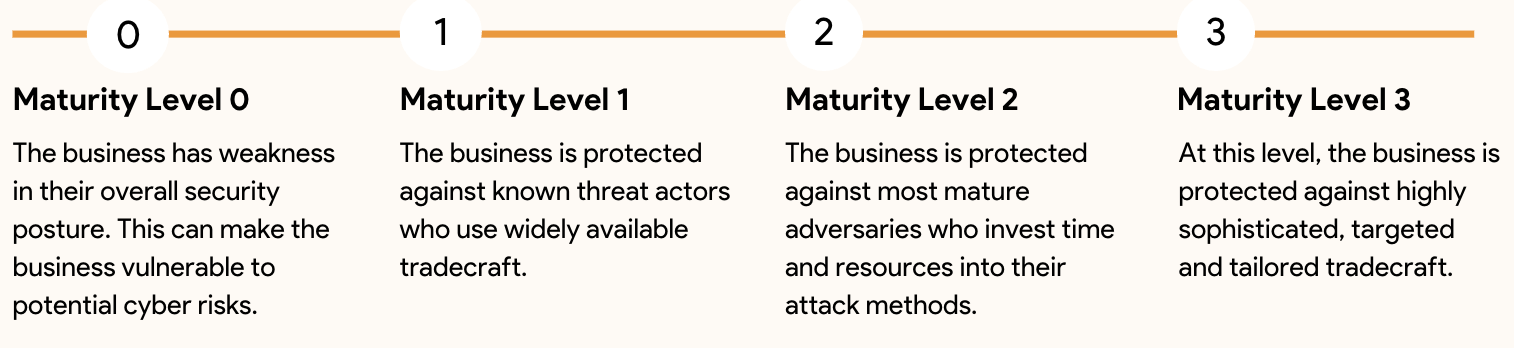
Essential 8 Maturity Model
Organisations that implement Essential Eight can track their compliance through the maturity model and invest in stages to achieve your security goals.
Essential Eight Core Mitigation Strategies
Aware of your organisation’s position on the maturity scale? Use the following eight mitigation strategies to secure your technology where it matters
Patch Application
Ensure that your applications are securely maintained.
Patch Operating Systems
Ensure that internet facing systems and services are secured.
Multi-factor Authentication
Protect accounts on all levels from compromise across business applications.
Restricting admin privileges
Secure the admin rights to your tech environment.
Application Control
Prevent malicious software from executing by establishing controls.
Restrict Microsoft Office Macros
Strengthen MS Office macros settings to avoid any abuse.
User Application Hardening
Protecting end-user system from malicious activities.
Perform backups regularly
Ensure the systems can be restored if any cyber incident were to occur.
Why AMARU for Essential Eight Implementation Services?
Get access to tailored assessments to identify your security posture.
Our team will help you set a baseline and identifying the maturity level your organisation needs to achieve.
Our compliance specialists will work with you priortise plans and steps to address relevant threats.
Use risk-based approach to have a cost-effective security management.

Case Study

We were really happy with how the whole process went. AMARU has great communication and are very easy to deal with. They were able to start the work quickly and gave us a comprehensive report with an informative presentation. We’ve already recommended them to others!

See our frequently asked cyber security questions below for help and advice.
What are the different Essential Eight maturity levels?
To assist organisations in determining the maturity of their implementation of the Essential Eight, three maturity levels have been defined for each mitigation strategy. The maturity levels are defined as:
- Maturity Level One: Partly aligned with the intent of the mitigation strategy.
- Maturity Level Two: Mostly aligned with the intent of the mitigation strategy.
- Maturity Level Three: Fully aligned with the intent of the mitigation strategy.
Is implementation of Essential 8 mandatory?
While it is not mandatory to adopt the Essential Eight, commonwealth entities are encouraged to assess their maturity levels against these strategies and implement them to the extent practicable.
The Australian government is increasingly encouraging and in some cases mandating its use, especially for organisations dealing with sensitive data or under specific regulatory requirements.
The primary goal of the Essential Eight framework is to help organisations mitigate cybersecurity incidents by strengthening their systems against threats. Compliance with this framework can help businesses meet various industry-specific security requirements.
Is Essential Eight only applicable to Australian businesses?
Yes, Essential Eight framework is developed by the Australian Signals Directorate (ASD) along with the Australian Cyber Security Centre (ACSC) to come up with a more localised framework to help organisations protect their systems from cyber threats.
While currently, Australian businesses are not required to comply with the Essential Eight, all government departments, agencies and local councils will at some point be audited against this framework and, it is recommended that these mitigation strategies be implemented in businesses as a baseline to help reduce the risk of cybersecurity incidents from occurring.
What is the difference between NIST CSF and Essential 8?
The NIST Cybersecurity Framework (CSF) and the Essential 8 are two different cybersecurity frameworks with some key differences:
-
Purpose:
- NIST CSF is a voluntary framework that provides a common language and approach for organisations to manage and communicate cybersecurity risk.
- The Essential 8 is a set of prioritised mitigation strategies developed by the Australian Cyber Security Centre (ACSC) to help organisations protect against cyber threats.
-
Scope:
- NIST CSF covers a broad range of cybersecurity activities across five core functions: Identify, Protect, Detect, Respond, and Recover.
- The Essential 8 focuses on a specific set of eight mitigation strategies to address the most common cyber attack vectors.
-
Adoption:
- NIST CSF is widely adopted globally, including by organizations in the United States and internationally.
- The Essential 8 is primarily used by organisations in Australia. However, it has now started to gain recognition in other regions like New Zealand as well.
-
Customisation:
- NIST CSF is designed to be customisable and adaptable to the unique needs and risk profiles of individual organizations.
- The Essential 8 provides a more prescriptive set of mitigation strategies that organisations are expected to implement.
In summary, the NIST CSF is a comprehensive cybersecurity framework that helps organisations manage and communicate their overall cybersecurity risk, while the Essential 8 is a more focused set of prioritised mitigation strategies to address common cyber threats. Both frameworks can be valuable, and organisations may choose to use them in combination or select the one that best aligns with their specific needs and risk profile.







